Shellcode Analysis
Malware Analysis — Advance Dynamic Analysis
Dynamic analysis involves executing the malware in a controlled environment to observe its real-time behavior and interaction with the operating system, networks, and files. This analysis focuses on monitoring system calls, registry modifications, API calls, and network traffic generated by the malware.
A sandbox environment, typically a virtual machine or an isolated system, is used to prevent accidental infections during testing. Analysts often utilize tools like Process Monitor, Wireshark, and API monitors to track the malware’s runtime activities. Behavioral patterns such as file creation, persistence mechanisms, command-and-control (C2) server communications, and exploitation of system vulnerabilities are documented to identify its purpose and potential impact. Dynamic analysis is particularly effective in identifying polymorphic or obfuscated malware that changes its code structure to evade static analysis.

Shellcode Analysis
Shellcode analysis focuses on understanding small pieces of malicious code, typically injected directly into memory, often used by attackers for exploitation or gaining control over a compromised system. Shellcode is often embedded in exploit payloads and is designed to execute commands or deliver additional malicious functionality. Analysts begin by disassembling the shellcode using tools like IDA Pro, Ghidra, or Radare2 to reverse-engineer its functionality.
Techniques such as decoding encoded payloads, identifying system calls, and mapping out control flow are common. Debuggers like OllyDbg or x64dbg allow analysts to execute the shellcode step by step to observe its behavior in memory. Understanding shellcode often reveals critical details such as targeted vulnerabilities, privilege escalation methods, or communication endpoints used by attackers. Since shellcode is typically compact and efficient, it requires meticulous analysis to uncover its full capabilities.
Start Analysis
First we need generate our shellcode using msfvenom.

To be able execute the shellcode we need wrap it into a stub, stub refers to a small piece of code or a program that serves as a placeholder or intermediary for larger, malicious functionality.
#include <stdio.h>
#include <windows.h>
unsigned char buf[] =
"\xfc\x48\x83\xe4\xf0\xe8\xc0\x00\x00\x00\x41\x51\x41\x50"
"\x52\x51\x56\x48\x31\xd2\x65\x48\x8b\x52\x60\x48\x8b\x52"
"\x18\x48\x8b\x52\x20\x48\x8b\x72\x50\x48\x0f\xb7\x4a\x4a"
"\x4d\x31\xc9\x48\x31\xc0\xac\x3c\x61\x7c\x02\x2c\x20\x41"
"\xc1\xc9\x0d\x41\x01\xc1\xe2\xed\x52\x41\x51\x48\x8b\x52"
"\x20\x8b\x42\x3c\x48\x01\xd0\x8b\x80\x88\x00\x00\x00\x48"
"\x85\xc0\x74\x67\x48\x01\xd0\x50\x8b\x48\x18\x44\x8b\x40"
"\x20\x49\x01\xd0\xe3\x56\x48\xff\xc9\x41\x8b\x34\x88\x48"
"\x01\xd6\x4d\x31\xc9\x48\x31\xc0\xac\x41\xc1\xc9\x0d\x41"
"\x01\xc1\x38\xe0\x75\xf1\x4c\x03\x4c\x24\x08\x45\x39\xd1"
"\x75\xd8\x58\x44\x8b\x40\x24\x49\x01\xd0\x66\x41\x8b\x0c"
"\x48\x44\x8b\x40\x1c\x49\x01\xd0\x41\x8b\x04\x88\x48\x01"
"\xd0\x41\x58\x41\x58\x5e\x59\x5a\x41\x58\x41\x59\x41\x5a"
"\x48\x83\xec\x20\x41\x52\xff\xe0\x58\x41\x59\x5a\x48\x8b"
"\x12\xe9\x57\xff\xff\xff\x5d\x48\xba\x01\x00\x00\x00\x00"
"\x00\x00\x00\x48\x8d\x8d\x01\x01\x00\x00\x41\xba\x31\x8b"
"\x6f\x87\xff\xd5\xbb\xf0\xb5\xa2\x56\x41\xba\xa6\x95\xbd"
"\x9d\xff\xd5\x48\x83\xc4\x28\x3c\x06\x7c\x0a\x80\xfb\xe0"
"\x75\x05\xbb\x47\x13\x72\x6f\x6a\x00\x59\x41\x89\xda\xff"
"\xd5\x63\x61\x6c\x63\x2e\x65\x78\x65\x00";
int main() {
// Allocate memory for the shellcode
void *exec_mem = VirtualAlloc(0, sizeof(buf), MEM_COMMIT | MEM_RESERVE, PAGE_EXECUTE_READWRITE);
// Copy shellcode to the allocated memory
memcpy(exec_mem, buf, sizeof(buf));
// Execute the shellcode
((void(*)())exec_mem)();
return 0;
}Compile it on linux machine using this command :
x86_64-w64-mingw32-gcc -o test.exe stub-popcalc.cnext transfer the binary to further analysis. open the x64dbg to perform debugging the stub.

Set the Breakpoint on VirtualAlloc WinAPI

Make sure the breakpoint was set.
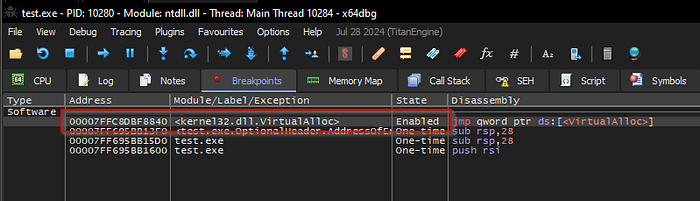
To continue press the F9 until we landed on our breakpoint on VirtualAlloc.
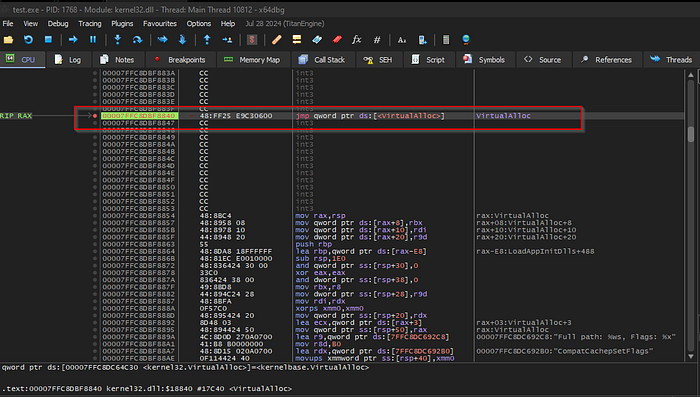
We will ignore the part inside VirtualAlloc process, so we need skip until the return.

After this press F8 until return from the function.

Byte FC mostly indicate that this is the first byte of shellcode.

The CLD instruction is essential in shellcode to ensure predictable and safe behavior of string operations, especially in unknown or inconsistent execution environments. By clearing the Direction Flag, the shellcode avoids bugs, ensures compatibility, and maintains a minimal footprint.
next wee need to dump the shellcode once we find it.


Once the dump shellcode success, next open the shellcode using the Binary ninja for further analysis.

if we deep dive further to the shellcode we will find sub_ca function, in this function we can find specific hash number that indicate winAPI with hex format. as you can see on this hex 0x876f8b31, if we google it. we can find this as kernel32.dll!WinExec

What is WinExec?
- Purpose: The
WinExecfunction launches an application. It allows you to execute a specified program, either as a console or GUI application. - Library:
WinExecis exported bykernel32.dll, a core system library in Windows that provides essential system APIs for process management, memory management, file handling, and other low-level operations.
Based on this finding, we can see on the low level what the API that called by the shellcode.
If you find value in this work and enjoy the content I create, consider showing your support with a crypto contribution. Every bit of support, no matter the size, helps sustain and grow.
Thank you for being part of this journey!

