Mobile Apps Pentesting: Android UnCrackable L2
Introduction
In this challenge we will try to crack the UnCrackable L2 android Apps, it’s basically same with the L1 but need more exploration on the low level. In this challenge we will do some reverse engineering using ghidra to find secret string to complete the challenge, ok let’s start.
Prerequisites
In this level we will proceed using this tools :
- Frida
- RMS
- Jadx
- Ghidra
Step-by-Step Guide to Cracking the Challenge
- Run the android emulator

- Install the UnCrackable L2 android Apps

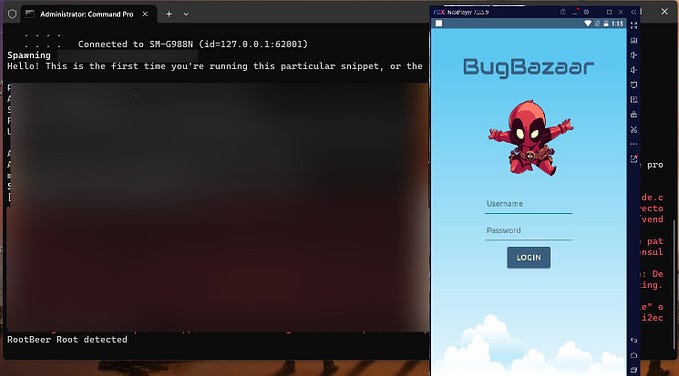
- If success installing the apps, on the first screen will display popup root detection. we will bypass this later.

- To bypass root detection, we will use Frida & RMS, first run your frida server on the emulator/device.

- Run your RMS apps and access the http://127.0.0.1:5000.

- Setup the RMS to invoke the android apps and run frida script from the RMS to bypass system.exit() function, so the apps will not exit when we click the ok button the

- When we run the script, the root detection will useless. tap the ok button.

- So in this state we have been complete half the challenge.
- For the next solution, I’ll using a few approach from this source.
- I’ll proceed using their solution and added my solution on the last.
- Firstly open the Jadx-gui to analyze the code.

- Pay attention on the MainActivity class and verify () method. when we analyze more, this method execute another class, on the class CodeCheck in this class is clueless.

- We want to try open
libfoo.sousing ghidra, let’s see what we get.

- We find interesting hex value and we find there is function
strncmp() - Using RMS we can find the parameter input from the int strncmp(char *__s1,char *__s2,size_t __n) function.
strncmp(param1,param2,size),this function comparing 2 param with specific size. in this case the size is0x17or 23 in decimal.

- so must input the 23 value length to the input form and we can write custom frida script to get the 23 bit value from memory.
var moduleName = "libfoo.so";
var functionName = "strncmp";
Interceptor.attach(
Module.findExportByName(moduleName, functionName), {
onEnter: function(args) {
var args1 = Memory.readCString(args[0],23);
var args2 = Memory.readCString(args[1],23);
send("Argument 1 : " + args1);
send("Argument 2 : " + args2);
}
});- we will input this 23 length string testtesttesttesttest123 and observe the RMS console you will find the secret key

- You Solve the challange!

- My approach is more simple, just find the juicy hex on the Ghidra and convert into ascii. and you will see the Secret key like below



![Maldev : [Evasion] Shellcode Injection and Fileless Execution](https://miro.medium.com/v2/resize:fit:679/1*NDzRNgdfpnmZ_mHscyI06Q.png)